Companies could go broke chasing the latest, greatest cybersecurity software tools or consultancy arrangements, and yet the greatest defenses most companies can employ are free. Awareness and training remain the most critical defenses for businesses of all sizes.
Training users to identify and avoid phishing and spearphishing attempts is perhaps the best cybersecurity training investment companies can make, as 95% of all attacks on enterprise networks are the result of successful spearphishing, according to the SANS Institute for Security.
Upward has observed a significant uptick in spearphishing attacks in recent months, and the sophistication is alarmingly good. Phishing or spearphishing is a social engineering attack, where an email from a credible or trusted source is actually malicious. Usually it involves either a hijacked account or a spoofed account.
These emails look remarkably authentic and often have links or attachments within them that prompt you to willingly input a sensitive username and password– gotcha!
The messages often say something like:
- “This is your boss: There is an urgent matter, I need you to wire money to a vendor immediately. Don’t delay”
- “You have received an attachment from So and So, click here to access it.”
- “Attached is a fax or voicemail attachment.”
Here is an example of a recent phishing attachment an acquaintance of Upward sent us:
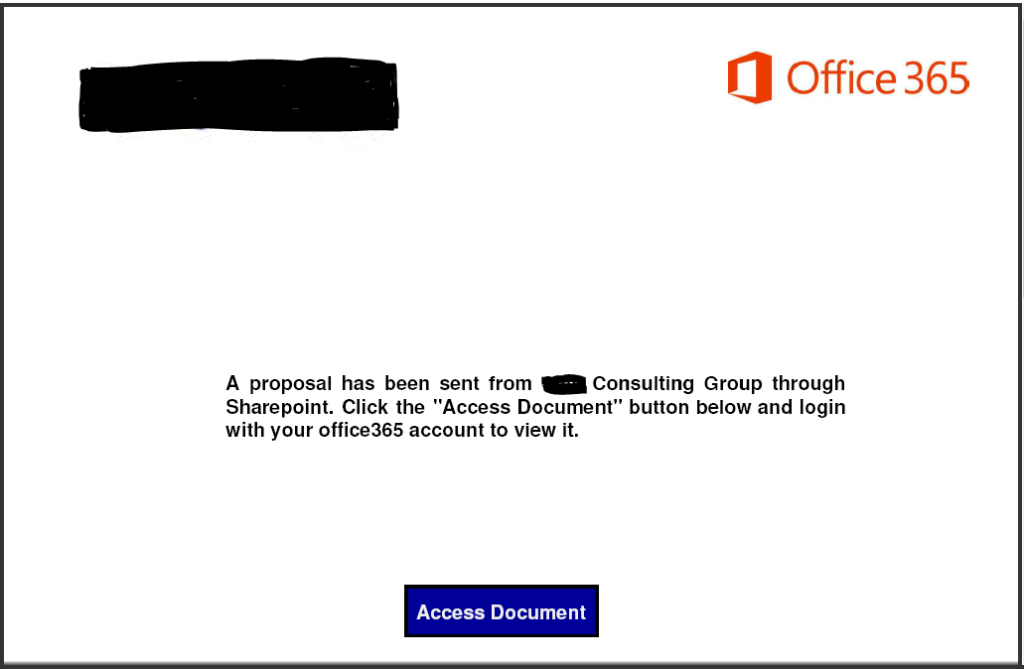
In the message, the person mentioned a proposal they wanted us to review. (We hadn’t solicited a proposal for anything recently, but have worked with them in the past.)
We responded: Have you been hacked? I wasn’t expecting anything from you.
Within moments, we got the response: We have a new proposal offering at ABC Consulting Group and I thought we should send it to you first to view, please download first view to be more elaborate. Thanks for the heads up!
If we were to have clicked the link, it prompts you for your email and password just like it normally would for a Microsoft file. Once you enter your username and password, your entire system is immediately compromised, and you have officially been breached. This type of message is alarmingly common, and because its coming from a trusted source, it passes right through spam filters.
Here are the two best ways to protect your company and yourself from this:
1. Exercise caution and vigilance
The best protection money can buy is an aware and cautious workforce. Every time you get an email attachment or request from someone you weren’t immediately expecting, pause, look at it carefully and perhaps ask a co-worker to take a look as well.
In the case of the above message, we immediately reached out to the person who sent it by phone to confirm and waited for her response. She texted back within a half hour letting us know she was living in a nightmare as dozens of her contacts were reaching out to figure out what was happening.
Always helps to be cautious.
2. Implement Multi-factor Authentication (MFA)
If your company has already implemented MFA, bravo! If not, we consider this to be perhaps the lowest hanging technical step available to secure a company from phishing attacks. With MFA, anytime a person wants to access your Office 365 account outside your network, they need a second form of verification. This renders the username and password you accidentally gave the bad guys completely useless.
Upward Technology Cybersecurity has a robust and thoughtful set of processes and solutions to help secure your environment, maintain compliance, and sleep well at night. Please reach out to sales@moveitupward.com to request more information or visit our website to learn more.






Leave A Comment